연구실에서 AI보안 쪽 공부할 때 공격에 대해서만 공부했던 거 같아서 방어 기법에 대해 궁금해졌다. 이번 주 논문으로 당첨 👊
💬 논문 내용과 이 글에 대한 의견 공유, 오탈자 지적 환영합니다. 편하게 댓글 남겨주세요 !
원문 : https://arxiv.org/pdf/1704.01155.pdf
Abstract
이전 연구들은 adversarial example을 방어하기 위해 DNN(Deep Neural Network) 모델을 개선(모델 자체를 수정해야 함)하는 것에 초점을 맞췄지만 성공이 제한적이고 계산 비용이 높다는 단점 존재
→ adversarial examples를 탐지함으로써 DNN 모델을 강화할 수 있는 Feature Squeezing 방식 제시
Introduction
- 분류기가 adversarial inputs을 탐지한다면 사용자에게 경고를 보내거나 fail-safe action을 취할 수 있기 때문에 공격 시도를 탐지하는 것은 정확한 결과 예측만큼 중요하다.
- 우리 연구는 입력 샘플을 변경하되 모델 자체는 변경하지 않는다는 점에서 이전 연구들과 차이가 있다.
- Feature squeezing 방식은 불필요한 입력 공간을 제거하여 공격자가 adversarial example을 생성할 기회를 줄인다.
- Feature squeezing의 핵심 아이디어는 원래 샘플에 대한 모델의 예측 결과와 squeezing을 거친 샘플에 대한 모델의 예측을 비교하는 것이다.

Background
Defensive Techniques
1) Adversarial Training : 발견된 adversarial input과 adversarial input에 대응되는 ground truth 레이블을 학습에 사용한다. 공격자가 미리 훈련된 공격 방식(= 모델이 알고 있는 공격 방식)만을 사용할 것이라고 보장할 수 없고 학습 비용이 증가한다는 단점이 있다.
2) Gradient Masking : ** cleverhans blog에 정리된 게 있는데 뭔말인지 모르겠어서 나중에 다시 정리해야겠다.
3) Input Transformation : 입력을 변환하여 모델이 입력의 작은 변화에 민감하지 않도록 모델을 강화하는 방법이다.
** 내용 추가 필요
Feature Squeezing Methods
A. Color Depth
논문 저자들은 비트 깊이를 줄이면 분류기 정확도를 손상시키지 않고 적대적 기회를 줄일 수 있다고 가정하고 초점을 맞춘 두 가지 표현은 8비트 그레이스케일, 24비트 색상으로 테스트 데이터셋에서 사용한다. 그레이스케일 영상은 각 픽셀에 대해 256(0~255)개의 색상 값을 제공한다. 8비트 스케일을 확장하여 RGB 채널로 컬러 영상을 표현할 수 있다.
1) Squeezing Color Bits : 사람들은 표시된 이미지를 natural image에 가깝게 나타낼 수 있다는 점에서 larger bit depth를 선호하지만, 사실 이미지 해석에 있어 large color depth가 필요하지 않은 경우가 많다(흑백 이미지 인식에 문제가 없기 때문). MNIST, CIFAR-10, ImageNet 데이터셋을 사용하여 bit depth squeezing을 관찰했다.

◻ Greyscale Images(MNIST) : 위 사진에서 가장 왼쪽에 있는 이미지는 원본(8비트) 이미지고 가장 오른쪽은 1비트 monochrome 이미지다. 1비트 이미지 feature space는 8비트 이미지의 1/128이지만 이미지를 분간하는 데에는 지장이 없다.
◻ Color Images(CIFAR-10, ImageNet) : 컬러 이미지도 MNIST와 비슷하게 비트 깊이가 감소하더라도 이미지를 구별할 수는 있지만 그레이스케일 이미지와 다르게 4 미만의 비트 깊이로 줄일 경우 이미지에서 일부 손실이 발생하는 것을 확인할 수 있다.
2) Implementation : 어떤 라이브러리를 썼는지, 어떤 식으로 구현했는지에 대한 내용이라 해석은 패스!
B. Spatial Smoothing(=blur)
1) Local Smoothing : 근처 픽셀을 사용하여 각 픽셀을 smooth하는 방법이다. Gaussian smooting, mean smoothing, median smoothing을 사용하여 인접 픽셀에 가중치를 부여할 수 있고 median smoothing은 L0 attack에 의해 생성된 adversarial example를 완화할 때 특히 효과적이다.
2) Non-local Smoothing : Local Smoothing보다 더 넓은 영역을 사용한다. **좀 더 자세히 알아볼 필요가 있다. 잘 모름 😵
C. Other Squeezing Methods
논문에서 사용한 방식은 아니지만 lossy compression, dimension reduction으로도 Feature squeezing이 가능하다.
Robustness
Feature squeezing이 adversarial examples를 효과적으로 탐지하려면 두 가지 특징(아래)을 충족해야 한다. 이 파트에서는 여러 방식의 feature squeezing이 이 특징들을 어떻게 만족하는지 확인한다.
① adversarial examples에 대한 squeezing
② **on legitimate examples, 분류기의 예측에 큰 영향을 미치지 않는 squeezing
◻ Threat Model
- Robustness를 평가하기 위해 학습된 target model에 완벽하게 접근할 수 있지만 영향은 못 미치는 powerful adversary를 가정한다. 또한 adversary는 feature squeezing을 인지하지 못하며 white-box attack 기술을 사용하여 모델의 오분류를 유도할 수 있는 입력을 찾고자 한다고 가정한다.
- Standalone feature squeezer의 robustness를 분석하긴 하지만, 공격자가 DNN 모델 공격 시 feature squeezing을 이용할 수 있기 때문에 방어를 위해 standalone squeezer의 사용을 제안하지는 않는다(권장하지 않는다 이런 느낌).
◻ Target Models : MNIST, CIFAR-10 및 ImageNet 데이터셋을 사용하며 각 데이터셋에 대해 최고 성능을 갖는 pre-trained model을 설정한다.
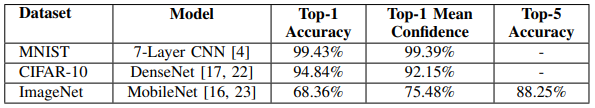
◻ Attacks : 총 11개 공격 방식에 대해 feature squeezing을 평가했고 각 targeted attack에 대해 두 가지 대상(t=L+1 mod #classes인 Next class, t=min(y hat)인 least-likely class)을 사용한다.
- t : target class
- L : ground-truth class의 index
- y hat : 입력 이미지의 prediction vector

Detecting Adversarial Inputs
Robustness 파트에서 feature squeezing이 legitimate examples에 대해 정확도 감소 없이 정확한 모델 예측을 얻을 수 있음을 확인했다. Feature squeezing 프레임워크의 기본 아이디어는 원래 샘플에 대한 모델 예측과 squeezing 후 샘플에 대한 동일한 모델의 예측을 비교하는 것이다. 두 예측은 유사해야 하며 동일한 모델이 두 샘플에 대해 눈에 띄게 다른 예측을 낸다면 입력 샘플은 adversarial일 확률이 높다.
A. Detection Method
DNN 분류기에 의해 생성된 prediction vector는 입력 샘플이 가능한 클래스에 속할 확률 분포를 나타낸다. 모델의 원본 예측과 squeezed sample의 예측을 비교하는 것은 두 확률 분포 벡터를 비교하는 것으로 확률 분포 비교 방법은 L1 norm, L2 norm, K-L divergence 등이 있다.
수식적인 내용은 표기가 살짝 귀찮아서 생략
B. Experimental Setup
◻ Datasets : MNIST 데이터셋에서 2,000개(legitimate example 1000개, adversarial example 1000개)+CIFAR10 데이터셋에서 2,200개+ImageNet 데이터셋에서 1,800개
- 각 탐지 데이터셋을 랜덤한 두 그룹으로 분할하고 하나는 detector 훈련을 위해, 하나는 validation을 위해 사용하였다.
◻ Squeezers : 먼저 각 squeezing 구성이 각 공격 방법에 의해 생성된 adversarial example에 얼마자 잘 적용되는지 평가한 후 defender가 공격자의 공격 방법을 알지 못할 때 공격 분포에 대해 잘 작동할 수 있는 구성을 선택해야 하는 시나리오를 고려한다.
'Artificial Intelligence > Paper' 카테고리의 다른 글
| EDA: Easy Data Augmentation Techniques for Boosting Performance on Text Classification Tasks (0) | 2022.11.07 |
|---|---|
| BERT: Pre-training of Deep Bidirectional Transformers forLanguage Understanding (0) | 2022.09.21 |
| Sequence to Sequence Learning with Neural Networks (0) | 2022.03.21 |
| Attention Is All You Need (0) | 2022.02.23 |
| Adversarial Examples in the Physical World (0) | 2022.01.27 |