사실 분석보다 직역에 가깝지만 내용 정리 및 집단 지성의 힘을 빌려 내가 잘 몰랐던 부분을 이해하기 위한 목적으로 적는다.
💬 논문 내용과 이 글에 대한 의견 공유, 오탈자 지적 환영합니다. 편하게 댓글 남겨주세요 !
원문 : https://arxiv.org/abs/1607.02533
Abstract
◾ 이 논문은 물리적 세계에서도 머신러닝 시스템이 adversarial example에 취약하다는 것을 보임
Introduction

◾ 머신러닝 모델은 오분류를 일으키기 위한 목적으로 만들어진 adversarial manipulation input에 취약하며 특히 테스트 시 모델이 미세하게 변경된 입력을 받는 것에 대해 매우 취약함
◾ 머신러닝 모델 M, 입력 샘플 C(변경되지 않은 깨끗한 상태의 샘플)가 있다고 할 때 C와 구별되지 않지만 모델이 제대로 분류하지 못하는 adversarial example A 생성 가능

◾ adverisarial example의 Transferbility property는 공격하고자 하는 모델에 access하지 않아도 공격이 가능함을 의미
🔍 Transferbility property
M1 모델의 오분류를 유도하기 위해 제작된 adversarial example이 M2 모델에서도 오분류를 일으키는 것
(**하나의 adversarial example로 여러 모델을 공격할 수 있다는 걸로 이해했다.)
◾ adversarial example이 실세계에서 카메라를 통해 생성될 경우 여전히 잘못 분류될 것인지는 (논문 나온 시점 기준) 이전 연구들로부터 밝혀지지 않음
▪ 논문 저자들은 물리적 세계&다양한 센서를 통해 데이터를 인식하는 기계 학습 시스템에 대해 adversarial example을 만들고 adversarial attack을 수행할 수 있는가? 하는 의문 제기
◾ 물리적 세계에서 adversarial example의 특성이 얼마나 잘 유지되는지 알아보기 위해 pre-trained ImageNet classifier로 실험 진행 후 휴대폰 카메라로 인식한 adversarial example을 classifier에 넣고 분류 정확도 측정
▪ 카메라를 통해 인식된 adversarial example도 모델이 잘못 분류하는 것을 확인함
Method of Generating Adversarial Images
Notation
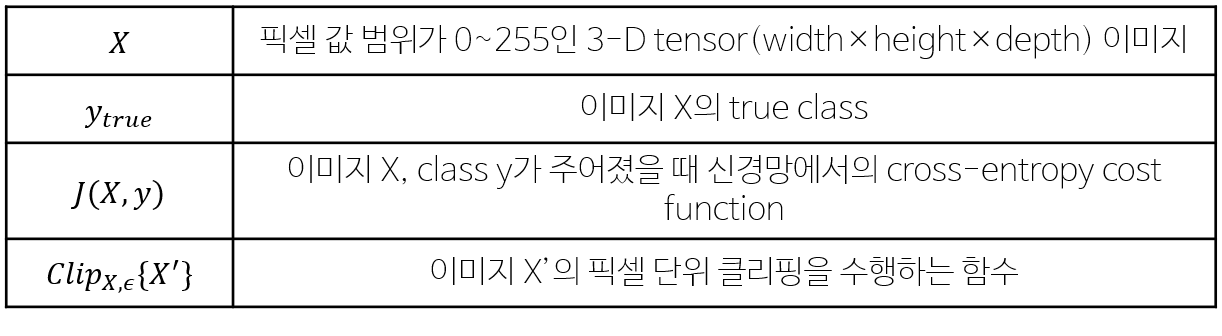
◾ Cliping equation

Comparison of Methods of Generating Adversarial Examples
◾ adversarial example이 실제로 잘못 분류된다고 보장할 수 없기 때문에 생성된 이미지의 실제 분류 정확도와 각 방법(fast method, basic iterative, iterative least-likely class method)으로 생성된 perturbation 유형을 이해하기 위해 실험적 비교 수행
▪ pre-trained Inception v3 classifier, ImageNet 데이터셋의 validation sample 5만 개 사용

Photos of Adversarial Examples
Destruction Rate of Adversarial Images
◾ 임의의 변환이 adversarial image에 어떤 영향을 주는지 알아보기 위해 destruction rate 개념 도입
🔍 Destruction rate
변환 후 더 이상 잘못 분류되지 않는 adversarial image의 fraction

Experimental Setup
◾ Clean image, adversarial image를 인쇄하고 인쇄된 페이지를 사진으로 찍은 후 사진으로부터 이미지를 잘라냄
▪ photo transformation이라는 용어로 정의(black box transformation으로 생각할 수 있음)
◾ Photo transformation 전후 clean image, advesarial image에 대한 정확도와 photo transformation의 대상인 adversarial image의 destruction rate 계산
Demonstration of Black Box Adversarial Attack in the Physical World
◾ 위에서 진행한 실험은 adversary가 모델에 접근 가능하다는 것을 전제로 하지만 실제 세계에서는 블랙박스 시나리오가 현실적
▪ transferbility property로 인해 adversarial example은 블랙박스 공격에 사용될 수 있으며 인쇄된 advesarial example도 오픈 소스 TensorFlow 카메라 데모를 속이는 것을 확인
Artificial Image Transformations
◾ 인위적인 이미지 변환에 대한 destruction rate를 이해하기 위해 대비/밝기 변화, 가우시안 블러, 가우시안 노이즈, JPEG 인코딩 적용
(**이미지 인쇄, 사진 찍기, 이미지 잘라내기는 단순환 변환이라고 볼 수 있기 때문에 대비/밝기 변화+a 적용했다는 의미인 듯)
Conclusion
은 패스!
정리하고 보니까 엄청 조잡하다. 다음 번에 다른 논문 정리할 때는 더 깔끔하게 적을 수 있기를 바라면서 🤐